The Perils of Phone Privacy – When Pragmatic Becomes Paranoid
Isn’t it convenient that you can tap a button and in seconds access the hourly forecast for your location? Or if you lose your phone its location can be triangulated to a definite address? On the contrary, think what that actually means. You are always traceable, and if someone wants to find you, they can. Without much technological lift, someone can pinpoint and acquire your exact location. “But I didn’t give my phone provider permissions to access my location!” you say, however it might not matter. In most cases the issue is not with your provider, but with the permissions you’re oblivious to within your phone or applications that provided immediate access to your location. Unless factory settings have been changed, there is a detailed, time-stamped map housed within your phone of all your destinations counting back as far as when you purchased your phone. We did a bit of in-office research on different devices regarding this, and we were able to see one employee’s day-to-day routes since late 2012 – she was unaware that her Android device was tracking this information.
In a recent study conducted by the Pew Internet and American Life Project, the 2,250+ participants were polled on their practices and knowledge pertaining to mobile privacy concerns. After learning of the amount of information publicly visible simply by downloading an application, one-third promptly uninstalled the app due to sensitive informational breach possibilities. In a nation-wide analysis of mobile trends, over 50% of mobile phone users have decided against downloading an application due to the information the developer or company requires the user to disclose. It is common practice for a developer/company to release a privacy policy in regards to the app. You can find this “Privacy Policy”, on Apple or Android devices, on the dedicated app page within your app purchasing store.
Case Study #1 : Snapchat
What about all those social-maybe-sometimes-should-be-secretive snaps you’ve sent? Cough, cough, Snapchat. In 2013, a digital forensics examiner named Richard Hickman uncovered that “expired” snapchats can actually be re-opened on Android devices as the metadata is stored as an actual file. Thus, your snapchats never disappear. This example is specific to Snapchat, a popular message application, but even if you don’t use this app, it’s a good example of how data can be stored without your knowledge.
Case Study #2 : The Missing Phone
Recently, a Media Genesis employee was off-site when she discovered that her phone was missing. It’s a newer model Android phone, which is helpful since you can usually track the location using Google’s Android Device Manager. Depending on the version of your Android OS, you may have to manually set it up in your phone’s settings, or it may automatically configure when you add a Google account to the phone.
Fortunately our team was able to locate and remotely lock the phone, the local police department was informed, and they went to the location to retrieve it. Your experience may vary depending on local law enforcement, not to mention local laws.

Let’s take a look at another scenario. Here is another one of our employees who has a Google (LG) Nexus 4 on T-Mobile, and is currently sitting at our office in Troy. However, if this phone was lost, he would have a few options as to find it or disable it.
1.) He could make it ring incessantly until found (which would be good if he had misplaced the phone in his house!)
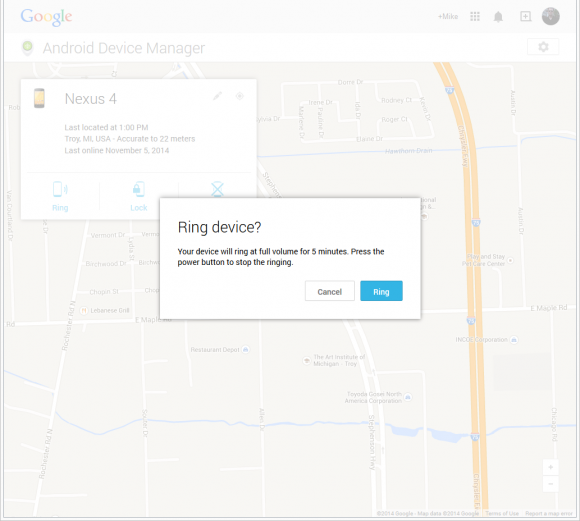
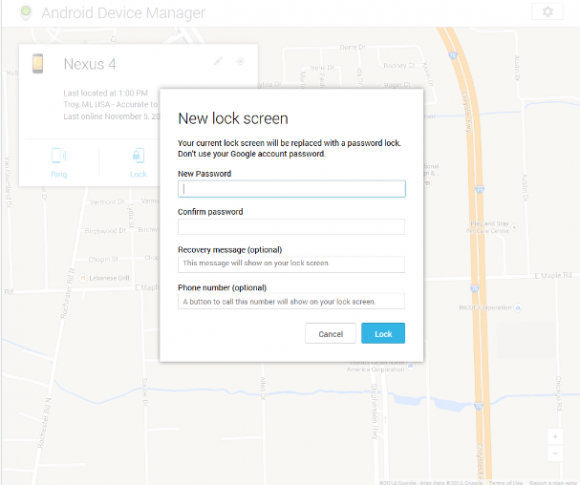
2.) He could remotely lock it with a code that only he knows, optionally displaying any message on the device, or even offer an option to call any phone number back from it.
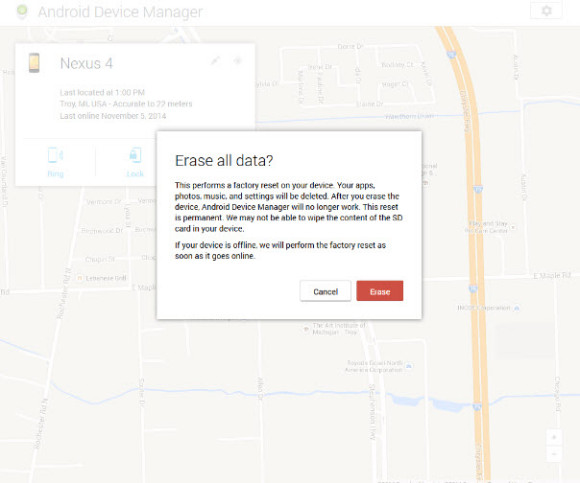
3.) Worst case scenario, if it wouldn’t be possible to get the phone back, he could remotely wipe it clean of all data.
Case Study #3 : Law Enforcement Accessibility
In a case of this technologically transgression turmoil, it’s not all negative. The ability to technologically investigate potential criminal suspects can give government/law enforcement a massive advantage. With proper warrants, government officials and police officers are able to track cellphone usage, triangulate a suspect’s position and/or read text messages from the suspect’s phone. On Wednesday, June 25th, 2014, the Supreme Court unanimously ruled that warrants are required for any kind of cellphone-based investigation by law enforcement or government after an arrest has been made.
Around 90 percent of all Americans have a cellphone. From mundane things such as solitaire to the intimate details of our personal lives, our phone keeps it all. We need to realize that in the year 2014, we walk with a heavy digital footprint in our pocket or purse. Our smartphone is a constant in our daily lives, and phones create an even larger and more precise footprint as it captures our communications, photos, habits and more. It’s important to remember to invest some time to get to know more about what information is captured or shared without your tacit knowledge. Also get to know how you can recover or find a device that contains so much information about you.


.png)
