The Ransomware War Rages On
Thanks to popular film and literature, we’re all somewhat familiar with the concept of thieves and kidnappers seizing control of something or someone and holding it for ransom. By just uttering the word “ransom,” you may immediately visualize a man picking up a phone and listening in horror as the voice on the other end utters – “We have your son. If you want him returned safely, we’ll need one million dollars by noon tomorrow!”

Fortunately, this extreme and terrifying scenario doesn’t play out too often in the United States, but there is another type of “ransom” that happens almost daily. A new form of extortion has been quickly spreading and affecting consumers every month. These scoundrels aren’t interested in capturing someone dear to you and holding them for ransom. Instead, they’re out to capture the data stored on your computer.
Your Computer Can Be Held Hostage… By Malware!
This latest trend in cybercrime and malware is known as “ransomware.” This treacherous software is often installed on websites with vulnerabilities, leaving a trap for unsuspecting visitors. If a visitor starts interacting with an exploited site and has outdated internet browser plugins – Java and Flash being very common examples – the malicious code may then be downloaded and infect the visitor’s computer. At this point, a visitor may soon discover that their machine is being held hostage.
Ransomware is not only becoming more sophisticated and difficult to break or remove upon infection, it is now trickier to identify at first glance. One type attempts to represent itself as a legitimate section of the United States government, claiming that your computer was locked for downloading and distributing illegal content. If you want to regain control of your computer, you are directed to first pay a “fine.” However, any payment is transferred to an account belonging to a hacker.
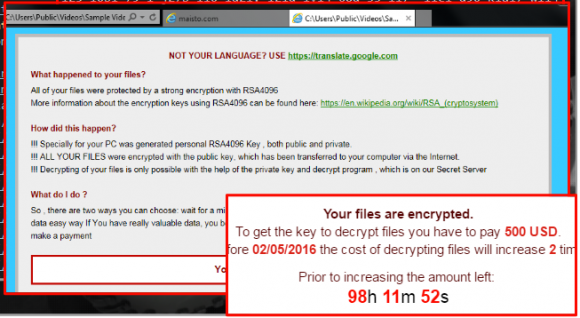
A more menacing type of ransomware is commonly referred to as a Cryptolocker. Typically, victims of Cryptolockers will first be notified that the contents of their hard drive are encrypted. This is followed by a ransom notice, usually asking for at least a few hundred U.S. dollars (or the bitcoin equivalent) to receive the encryption key in order for users to unlock their files. Some hackers will pile on the pressure, claiming that if the victim fails to pay the money within a couple days, they’ll significantly raise the ransom amount.
To learn more about the different types of ransomware plaguing the cyberworld, check out this video by ESET:
Revenge of the Cryptolockers
In 2015, we explored the rise of cyber extortion and some rather concerning ransomware events. Even the City of Detroit had fallen prey to cybercriminals that were asking for more than $800,000 in bitcoin in exchange for unencrypting a database held hostage. Unfortunately, ransomware cases such as these are only increasing with time in both frequency and severity.
Last month, the main website of a popular toy maker, Maisto, became the victim of a relatively new Cryptolocker version known as CryptXXX. According to Malwarebytes, the website was running an outdated version of the CMS Joomla and an exploit kit was capable of using the vulnerability to its advantage. The home page itself was infected and Maisto was forced to quickly place the entire website in maintenance mode to ensure the safety of its visitors.
Tips & Tricks for Avoiding Ransomware Threats
Much of the ransomware protection advice that started circulating around tech communities and blogs a couple years ago still rings true today. Recent patterns suggest a couple security measures are especially important to remember:
- Back-ups can save your life! Well, your computer’s life anyway. In some cases, the data stored on a personal computer may not be that valuable and many victims just let the hackers keep their data. But in many cases there are likely to be personal files, pictures, and videos stored on your computer that could be priceless. If you are infected and you store regular back-ups on an external source, you can simply restore your data and leave the bandits empty-handed while saving your content. Check out our previous article for quick tips on backing up your data.
- Make sure to keep your browser and its plugins updated. If you can’t or prefer not to update features such as Flash, Java, and Silverlight, then from a security perspective you’re much better off just disabling them.
- Anti-virus and security companies, like Kaspersky, are always trying to stay ahead of the game and improve Cryptolocker prevention kits. If your computer stores sensitive data, it’s worth investing in malware detection tools that are constantly on the look-out for ransomware and other intrusions.
CMS Maintenance is Crucial!
Ask anyone at Media Genesis and they will stress the importance of keeping your website updated. Last month, we talked about the importance of regular maintenance for WordPress and other content management systems. One of the key benefits to this is minimizing the risk of cyberattacks, such as the injection of ransomware.

Don’t forget! Maisto’s home page was held hostage because a security hole in their outdated CMS was exploited. The consequences of this outcome are not only public embarrassment, but undoubtedly a substantial loss in revenue.
All CMS platforms – including WordPress, Joomla, Drupal, and others – are especially susceptible to malicious attacks if they are not regularly updated. If you have a site based on a CMS and you’ve let maintenance slide over the years, it’s time to start upgrading your CMS and patching your website’s security holes. After all, we don’t want you to be forced to walk the same road to recovery as Maisto is enduring right now.
Think your site might be at risk or need an upgrade? Reach out to us; we can help you with general website maintenance, CMS updates, and all things web.


.png)
